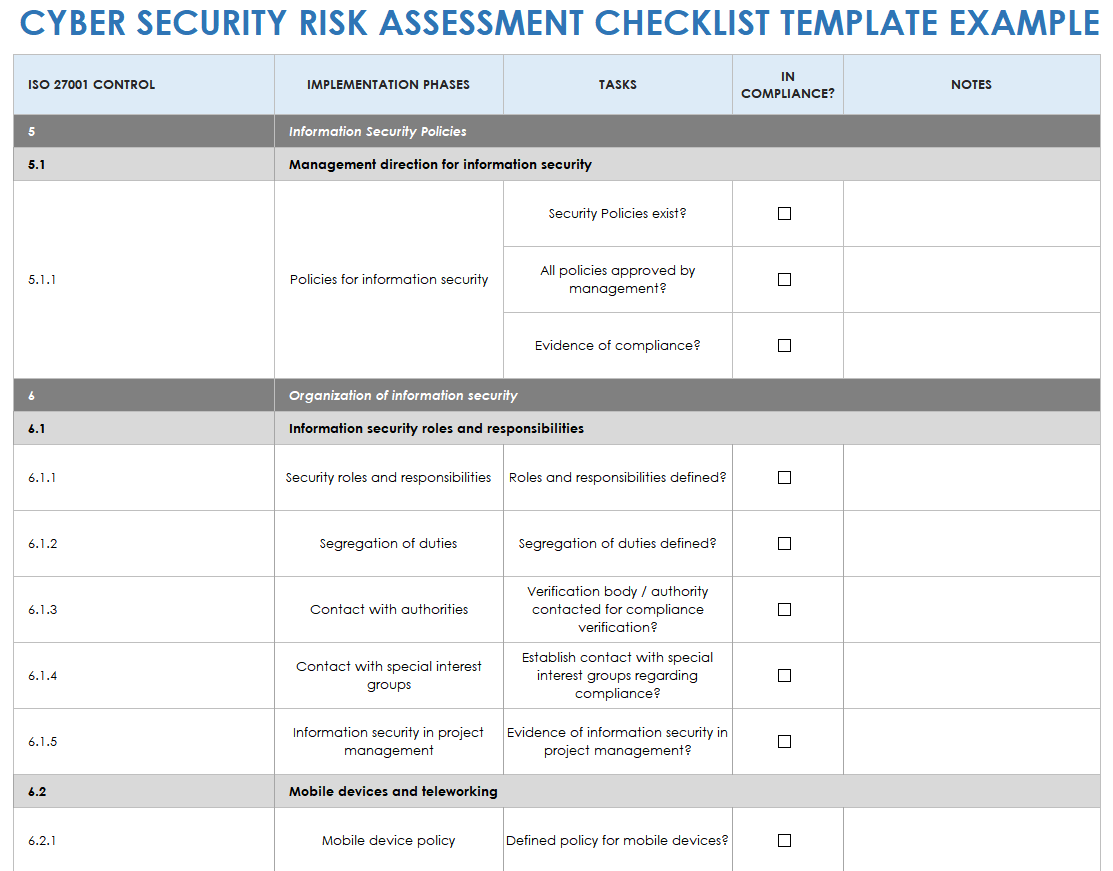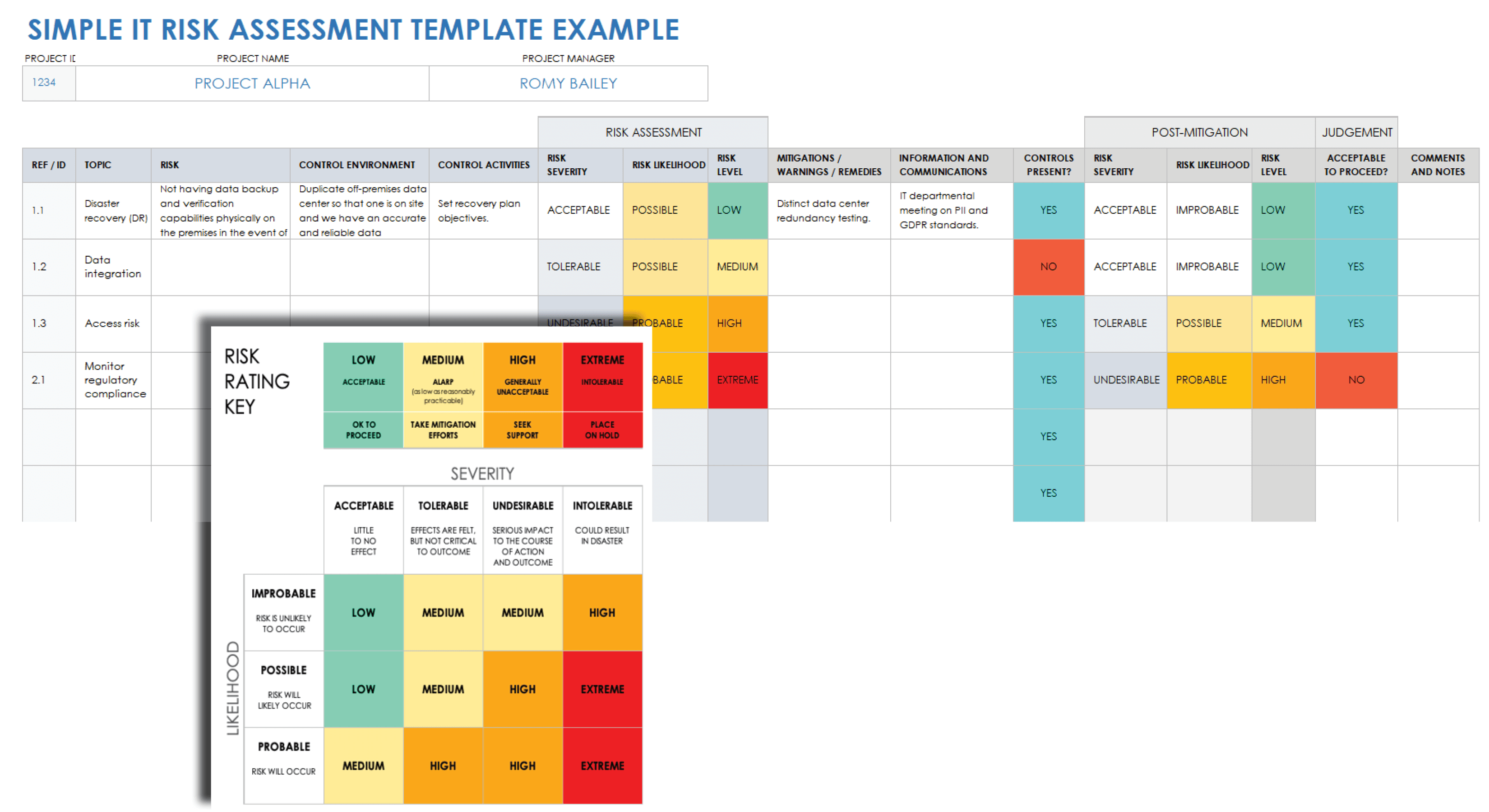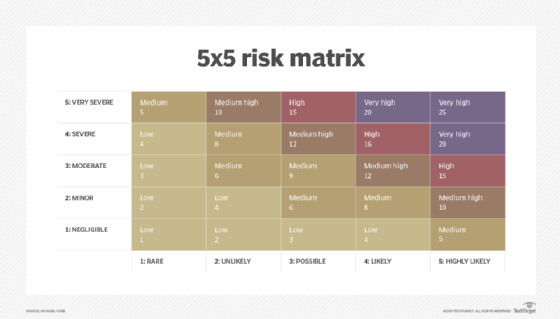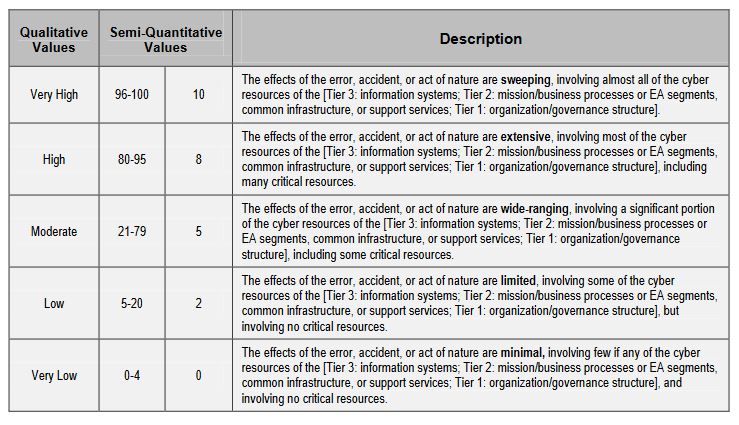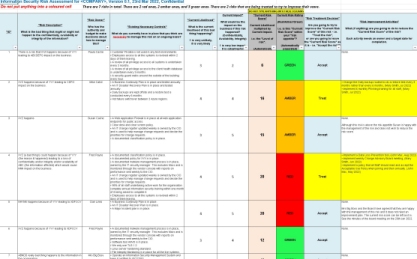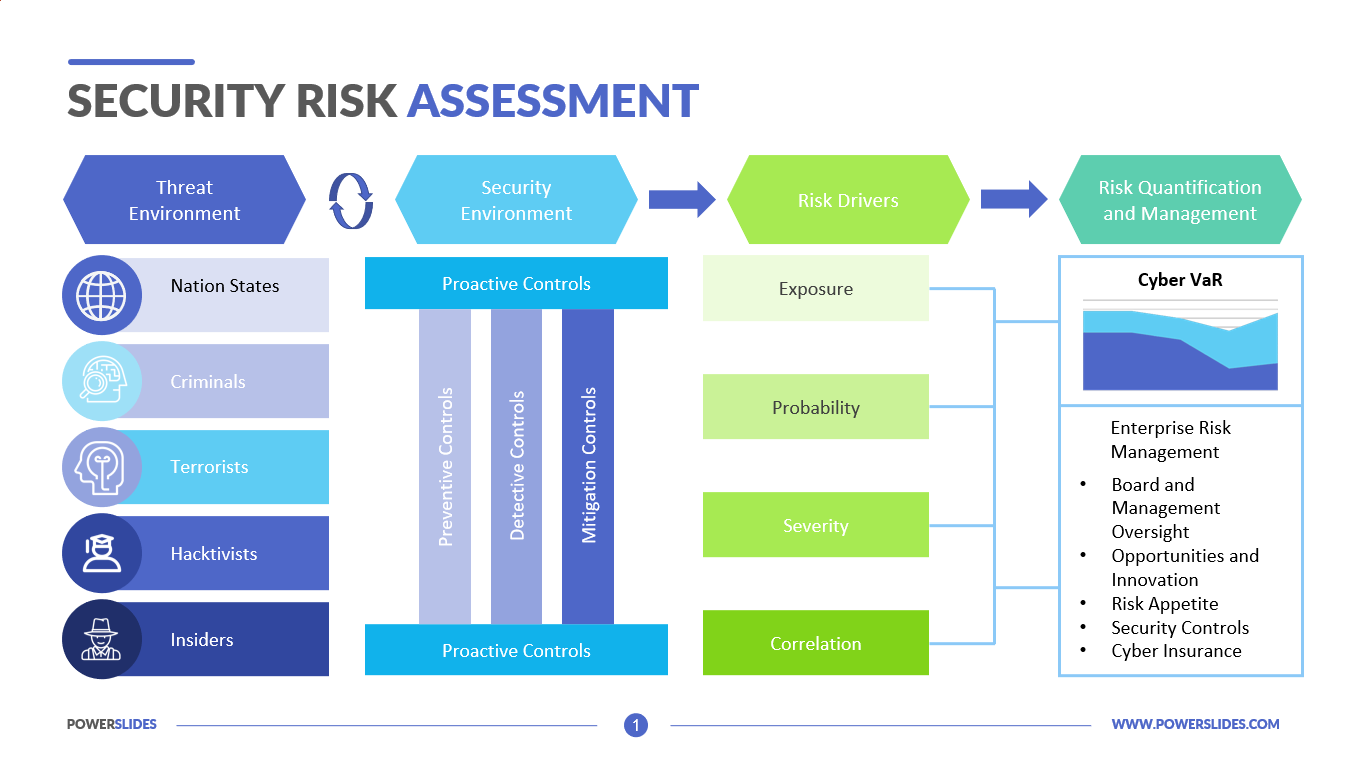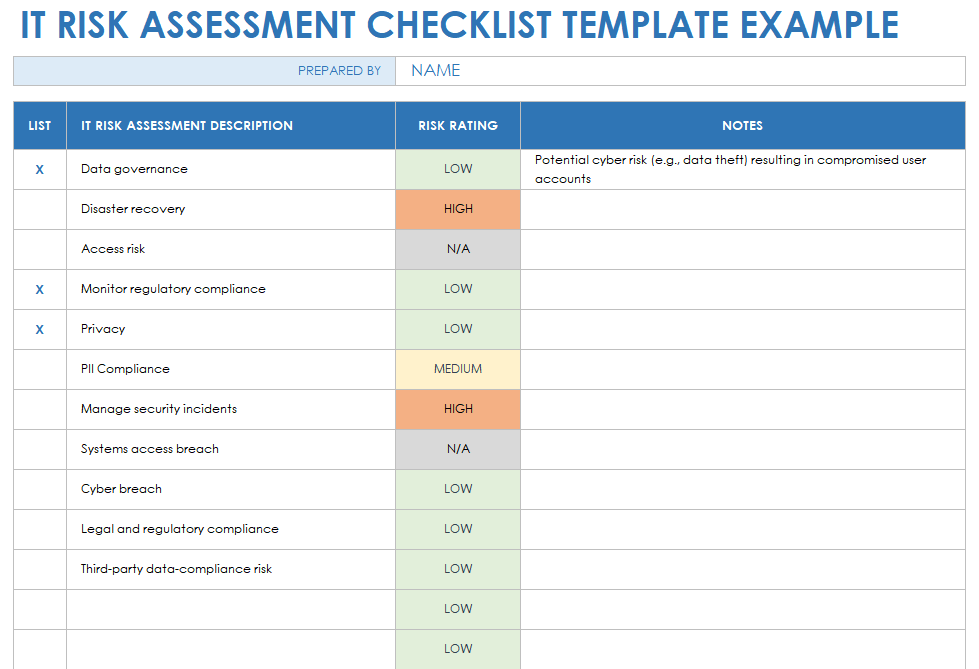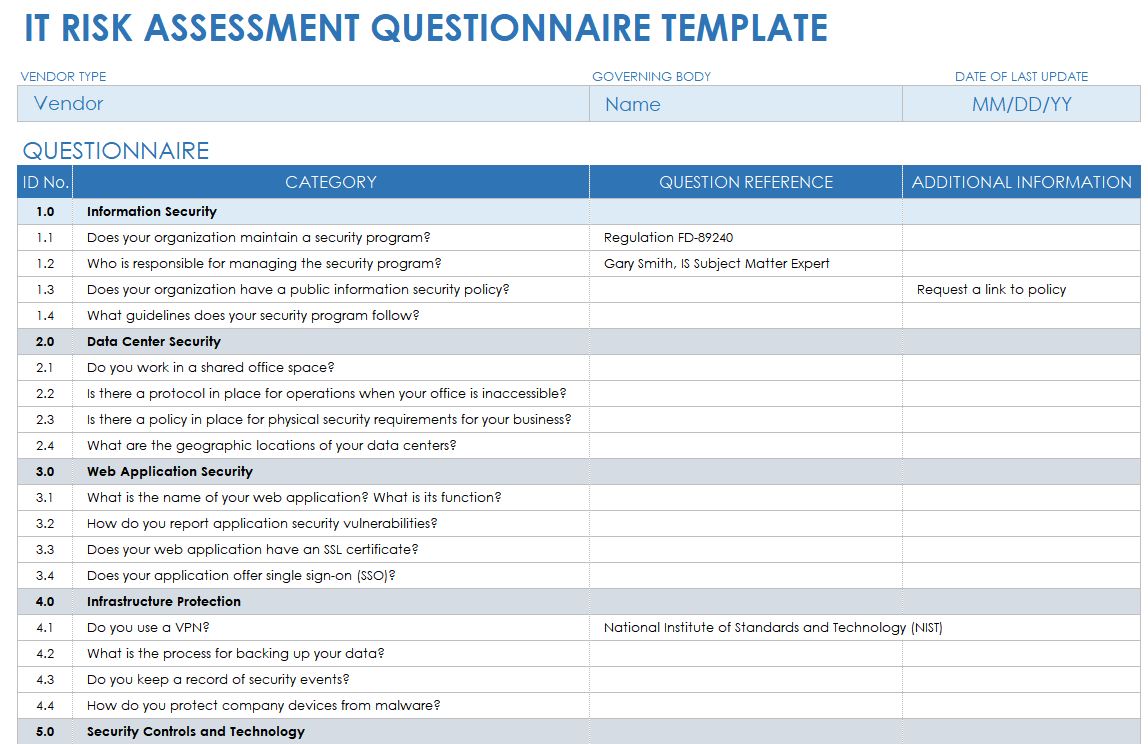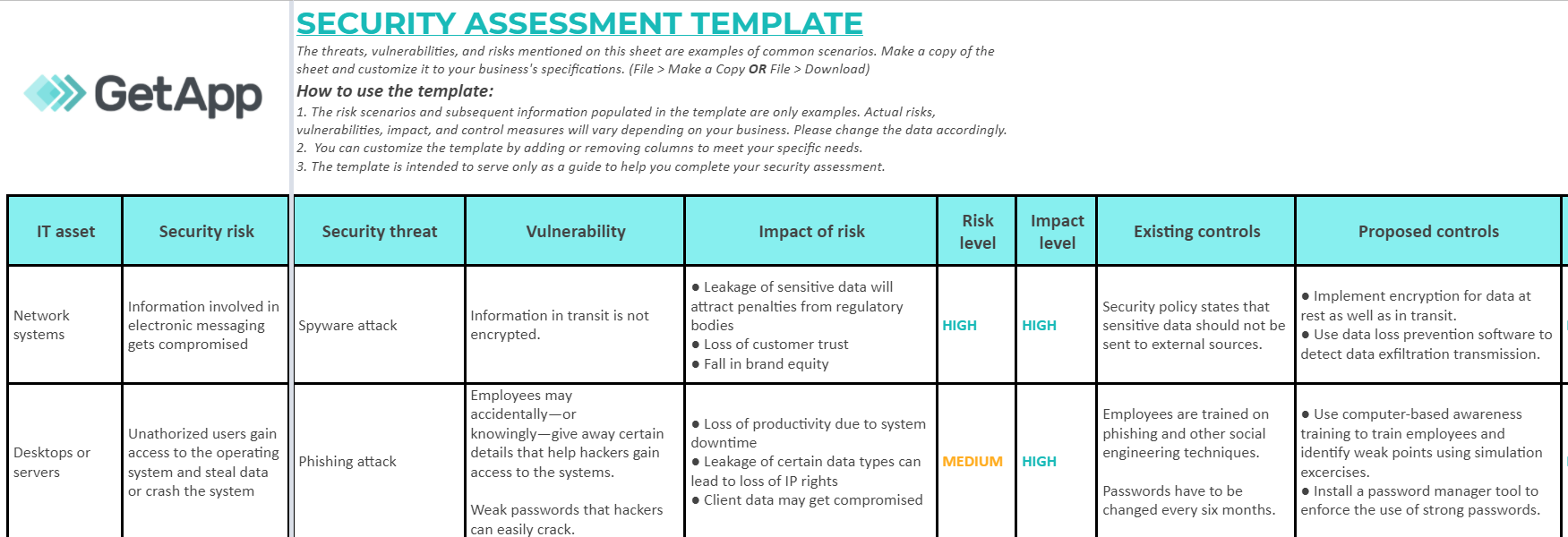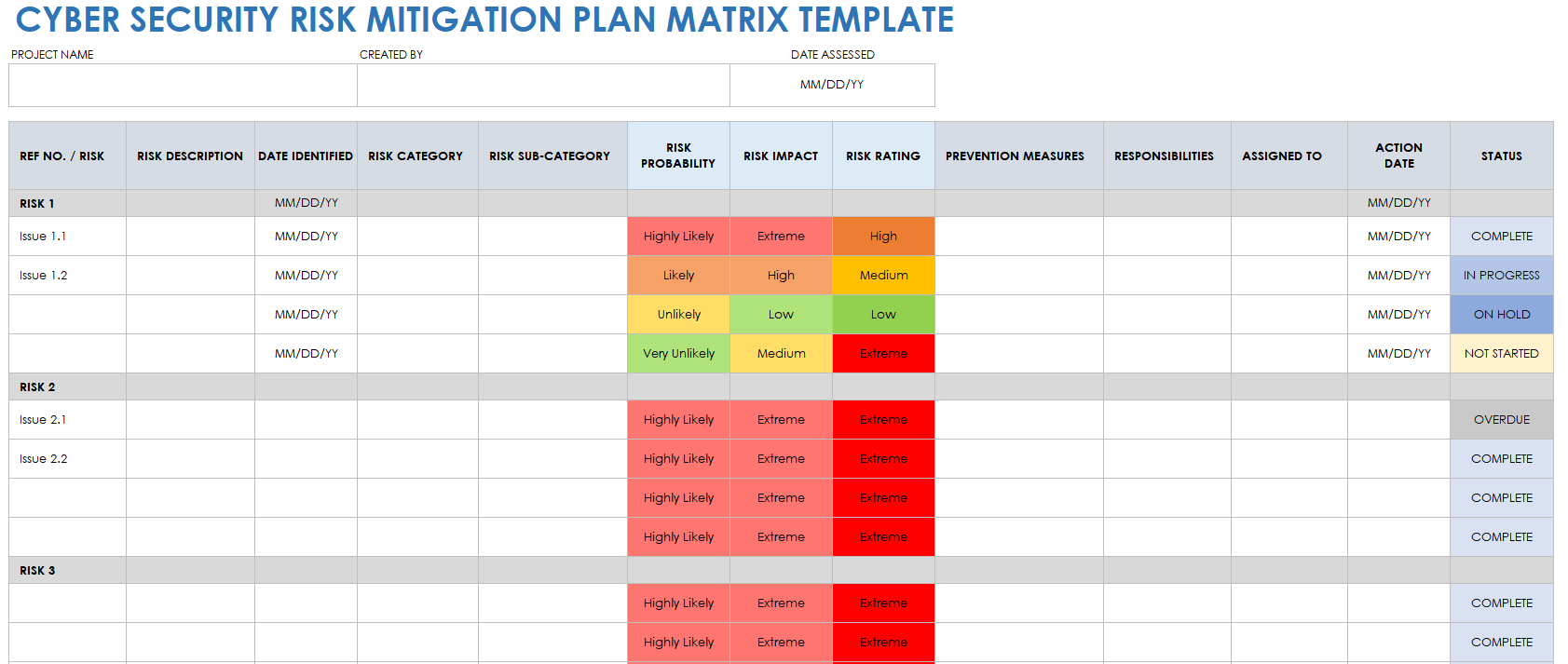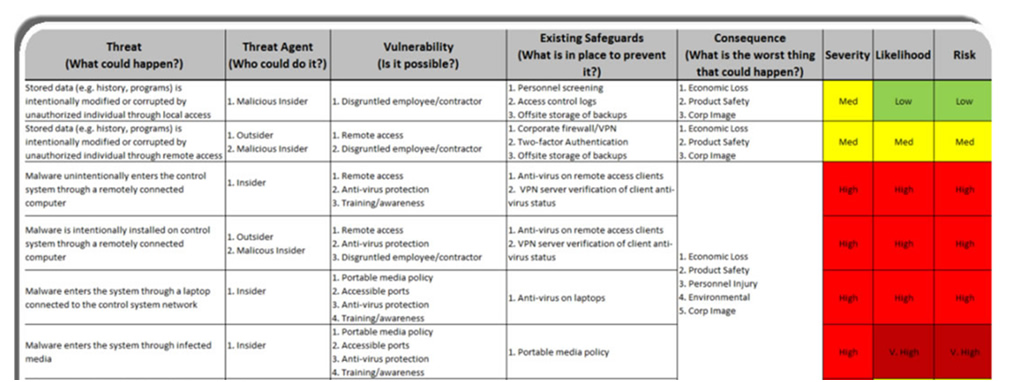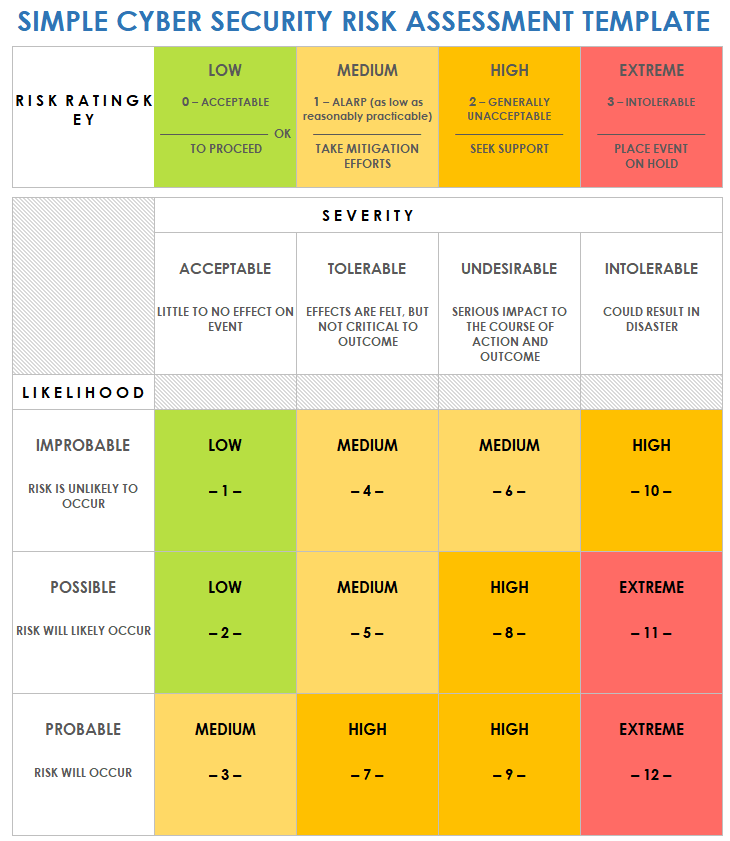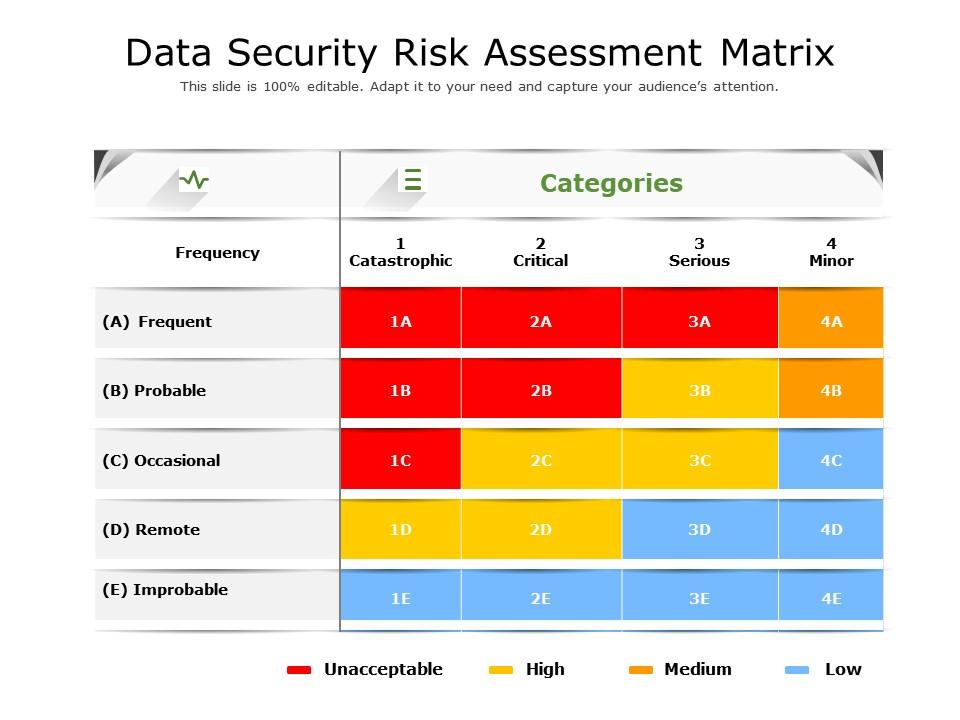
Data Security Risk Assessment Matrix | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Security Risk assessment Template Best Of 10 Sample Security Risk assessment Templates Pdf Word | Risk management, Security assessment, Assessment
Information Security Risk Assessment Worksheet Critical Ppt Visual Aids Icon | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

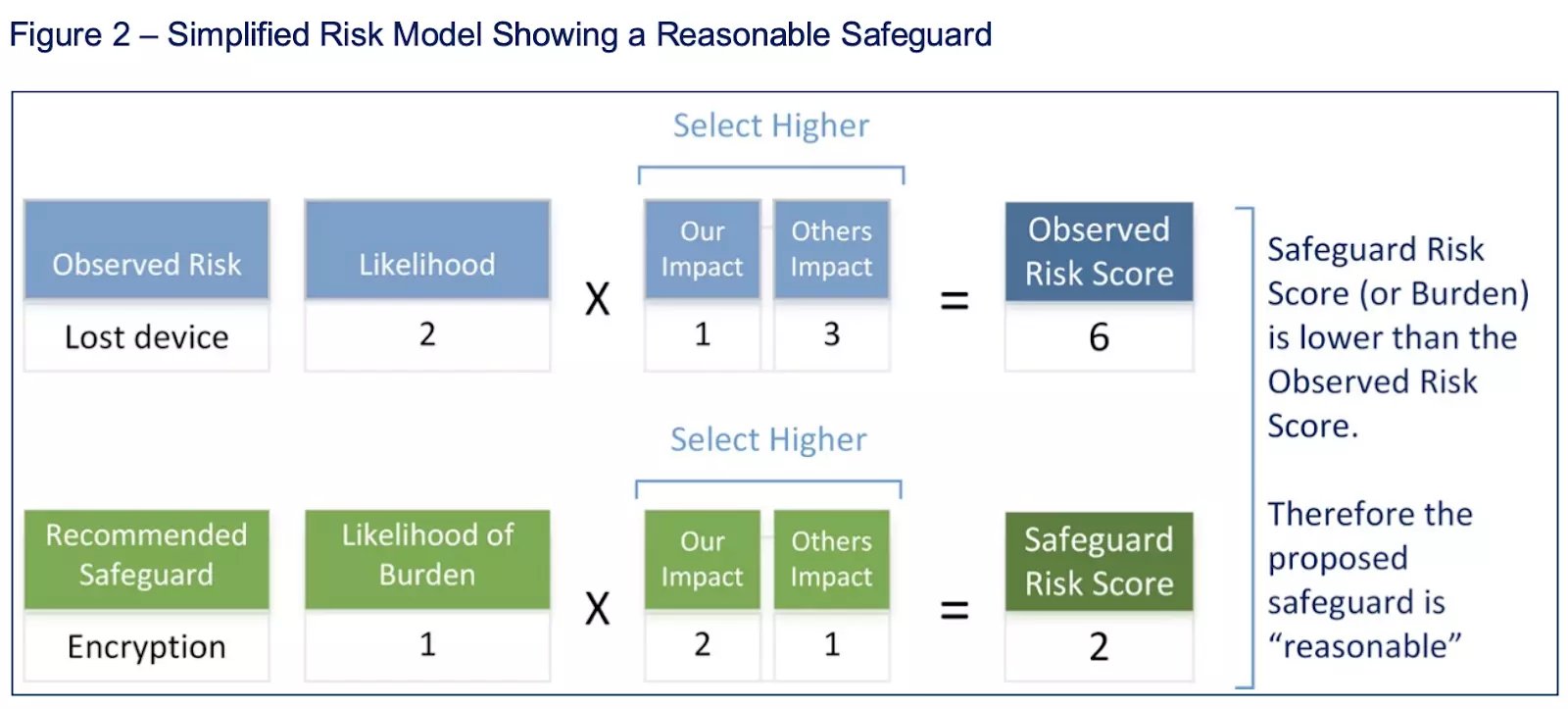
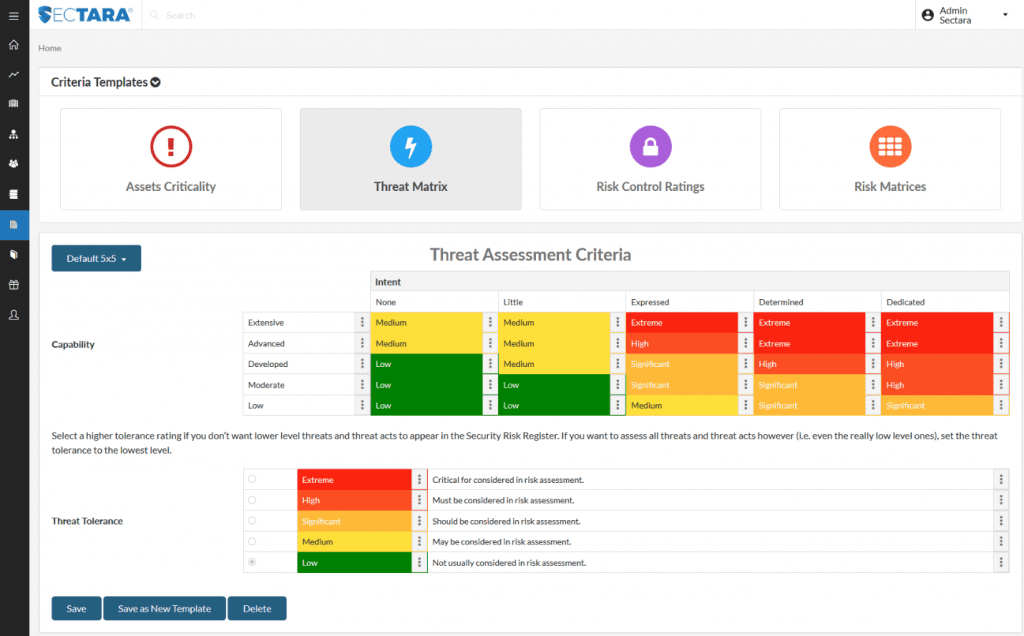
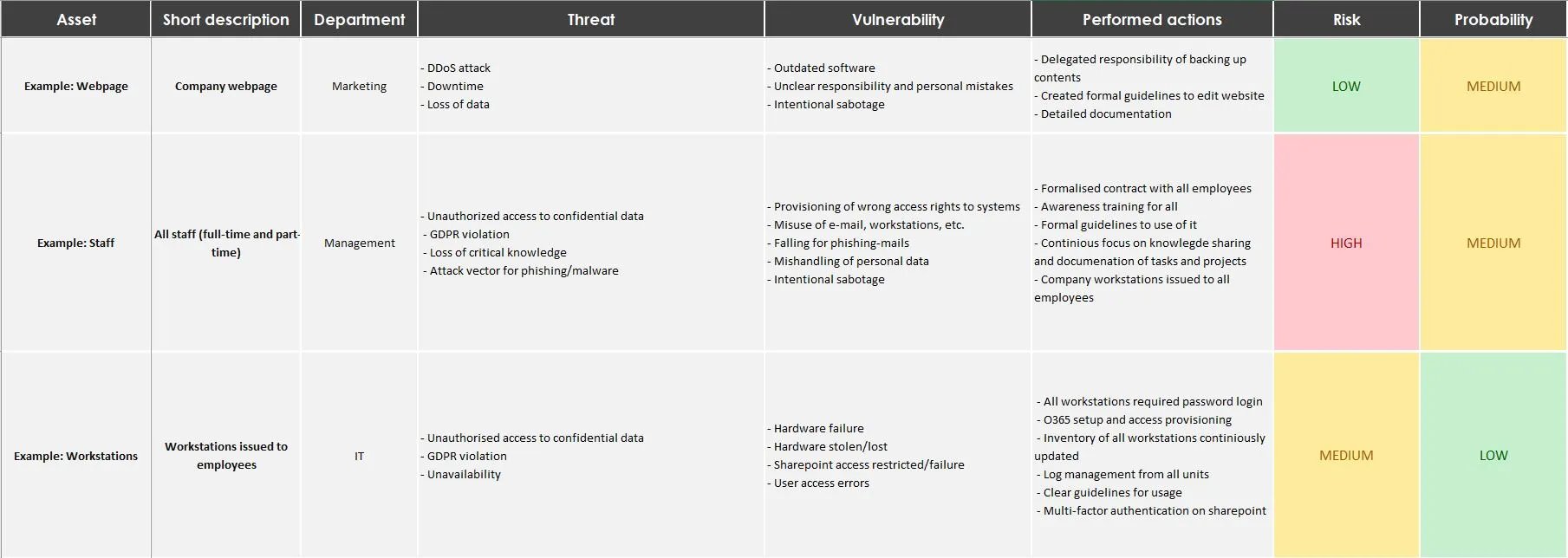

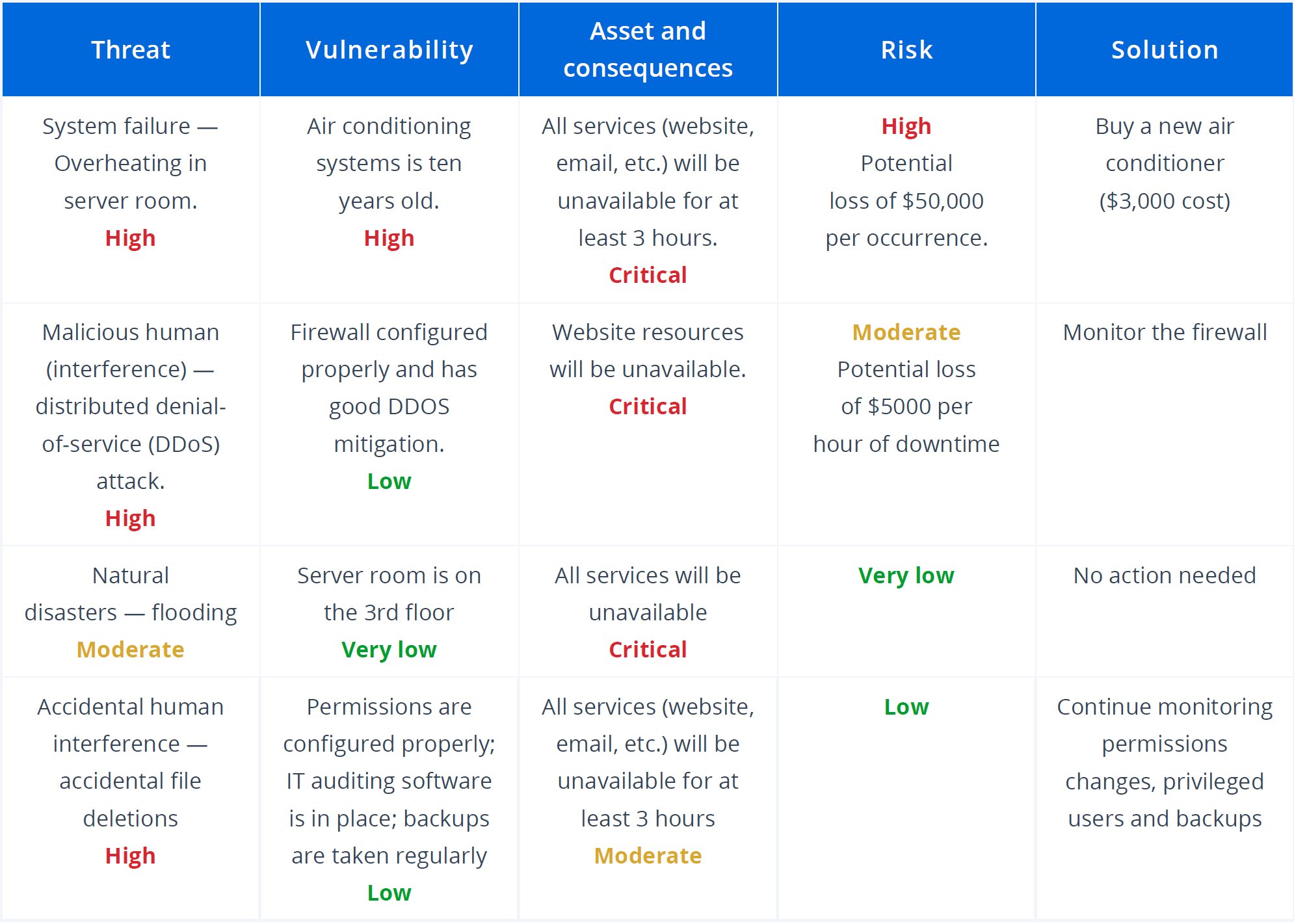
![PDF] Information Security Risk Assessment: A Method Comparison | Semantic Scholar PDF] Information Security Risk Assessment: A Method Comparison | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/648d7a0a2b2205bbb63d2baf4330d3c877a480a5/4-TableII-1.png)