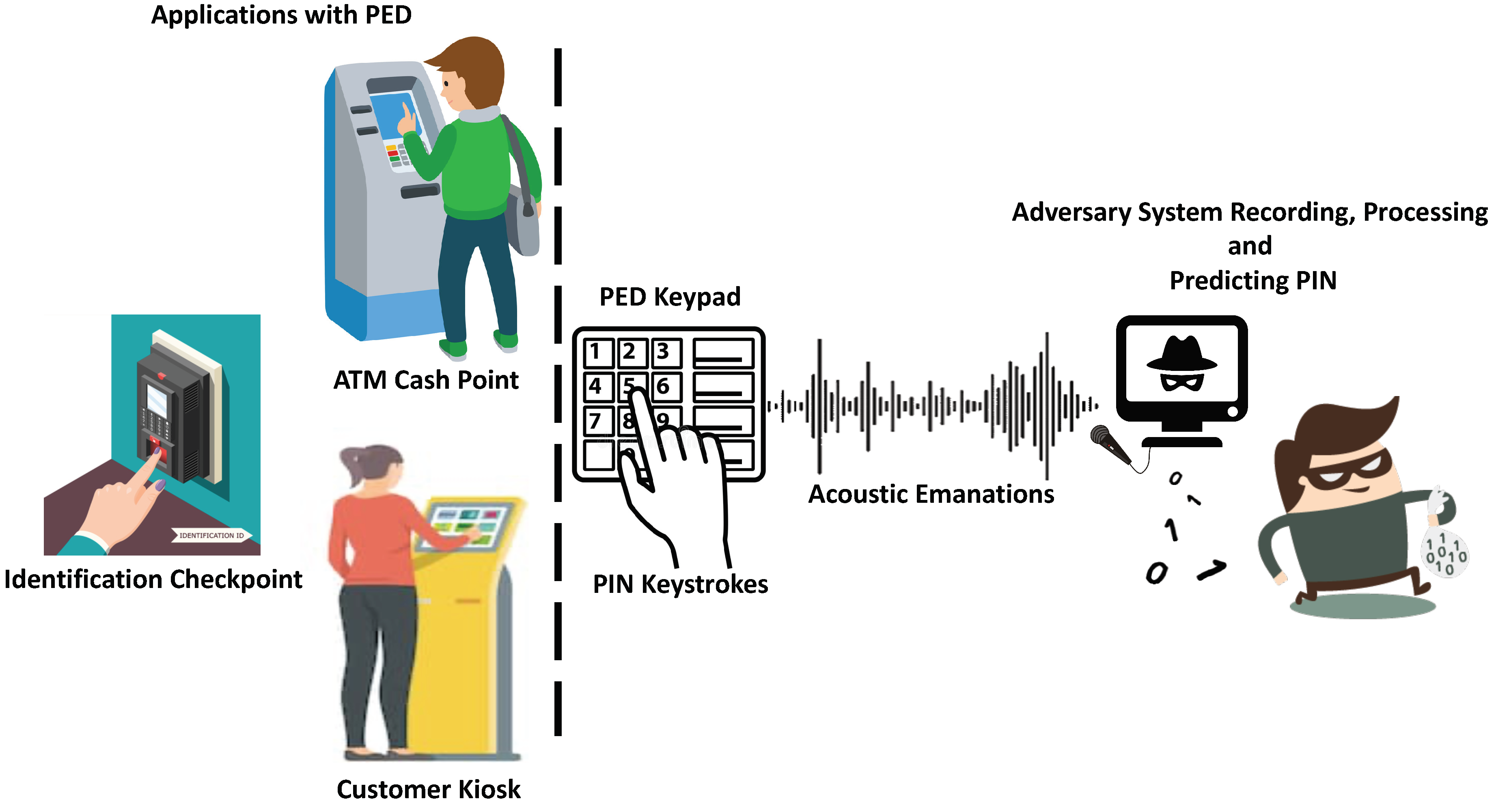
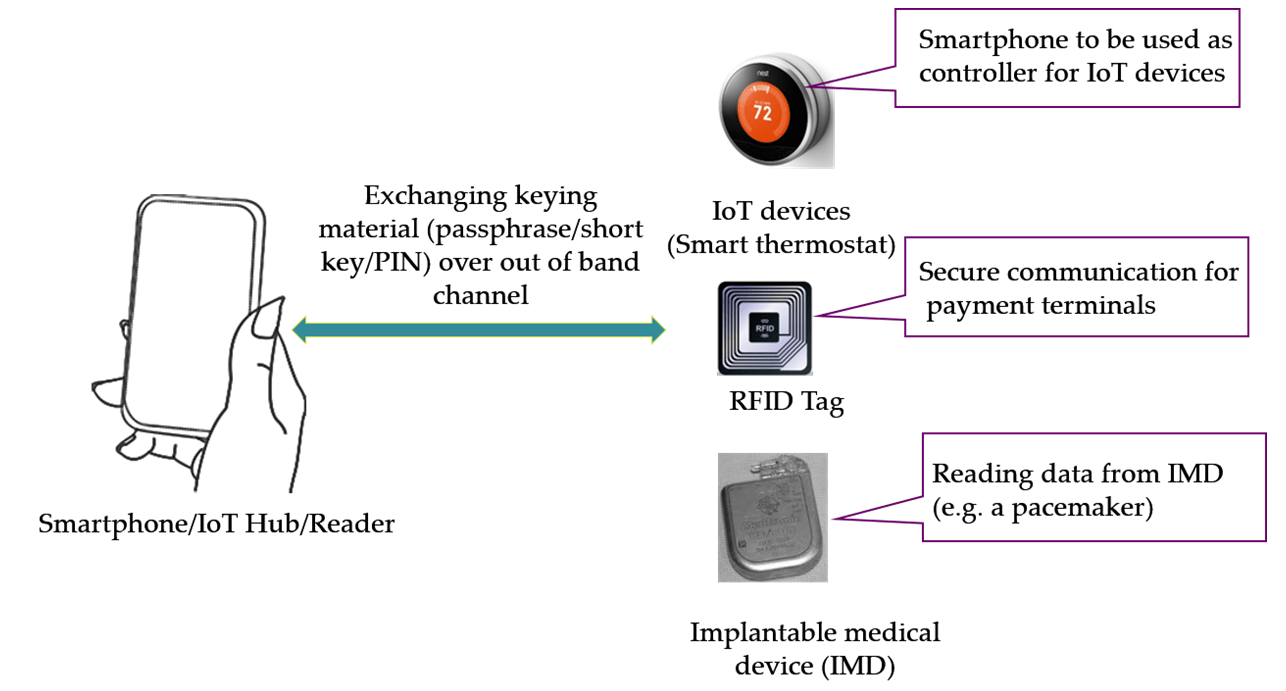
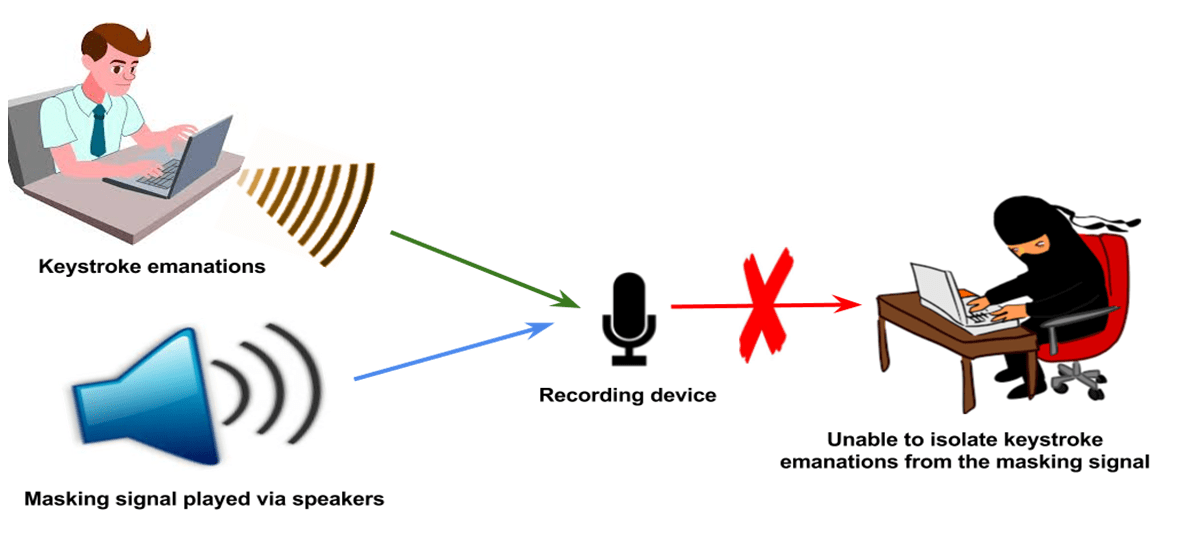
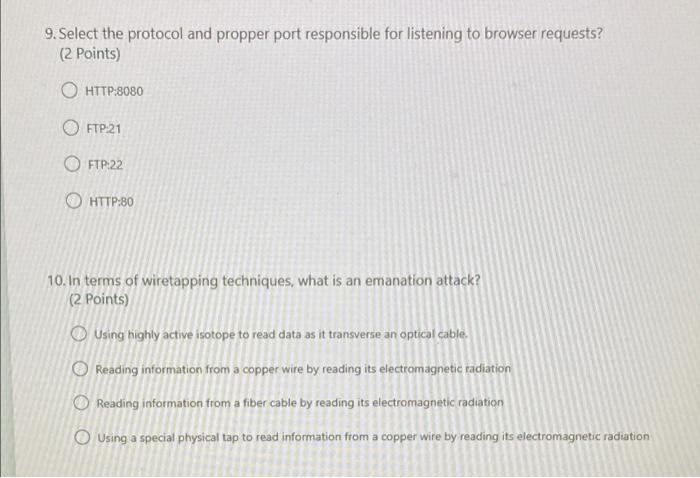
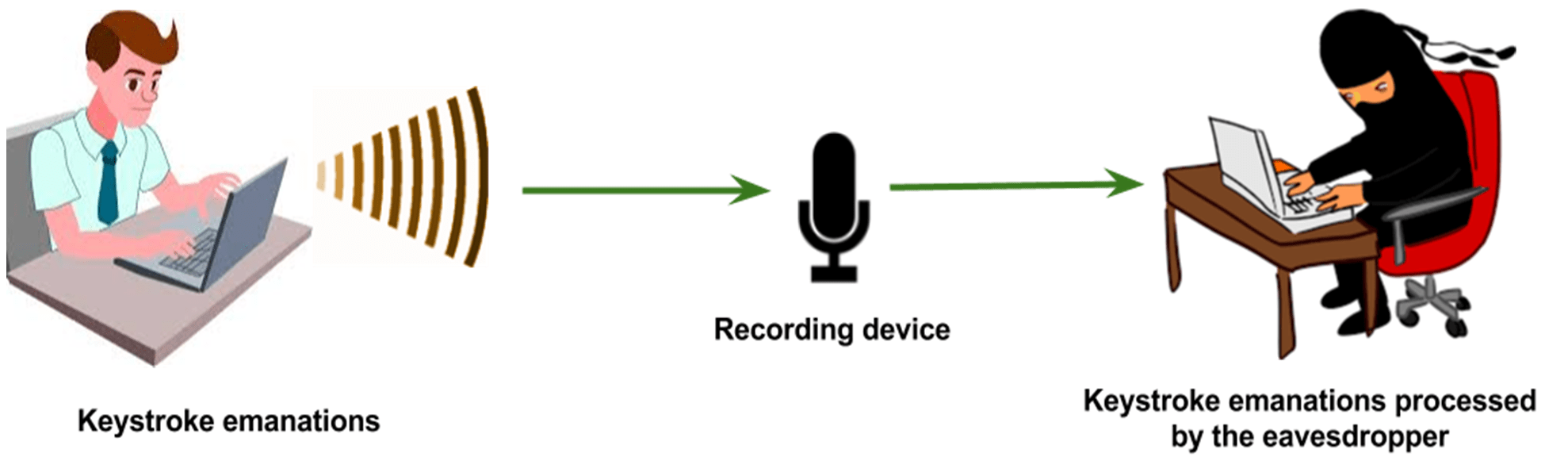
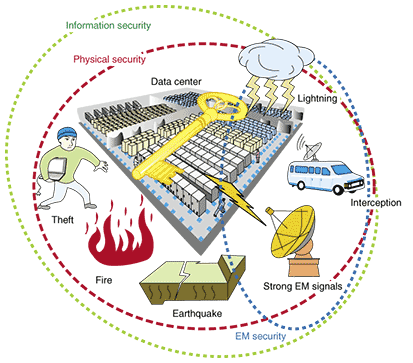
Unintentional Compromising Electromagnetic Emanations from IT Equipment: A Concept Map of Domain Knowledge

Radon Emanation Measured Data Along a Traverse Crossing Ahwaz Fault... | Download Scientific Diagram

IJERPH | Free Full-Text | Development of 222Rn Emanation Sources with Integrated Quasi 2π Active Monitoring

Radon Emanation Measured Data Along a Traverse Crossing Ahwaz Fault... | Download Scientific Diagram
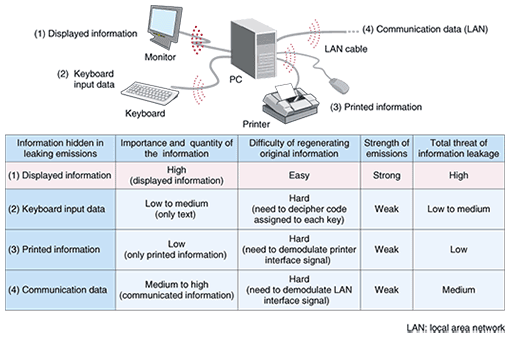
Countermeasures to Prevent Eavesdropping on Unintentional Emanations from Personal Computers | NTT Technical Review