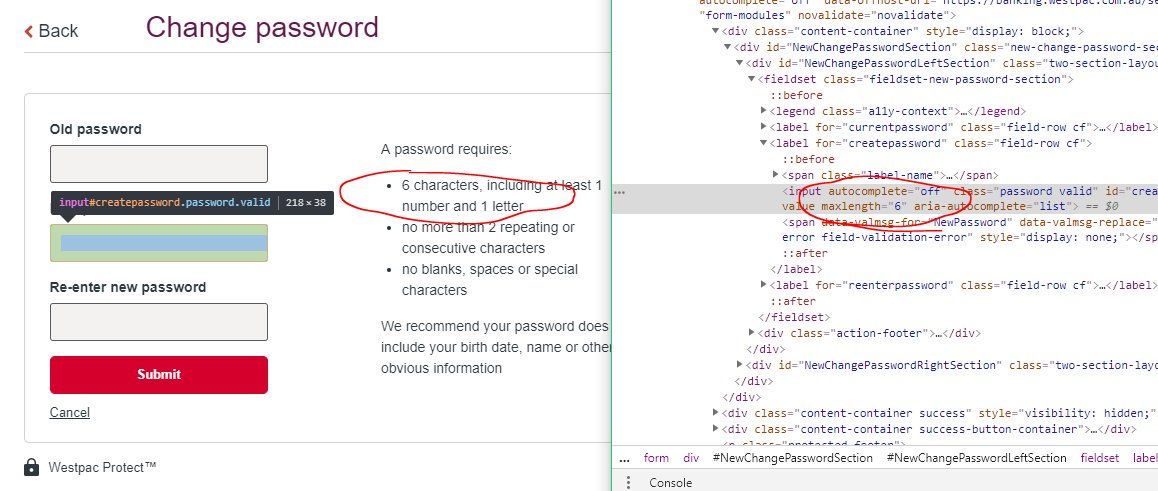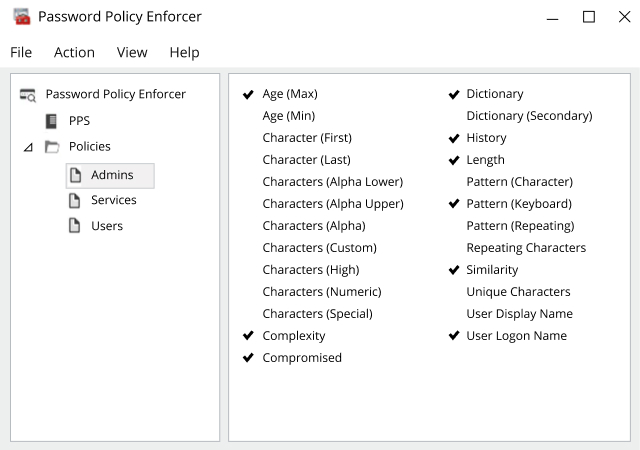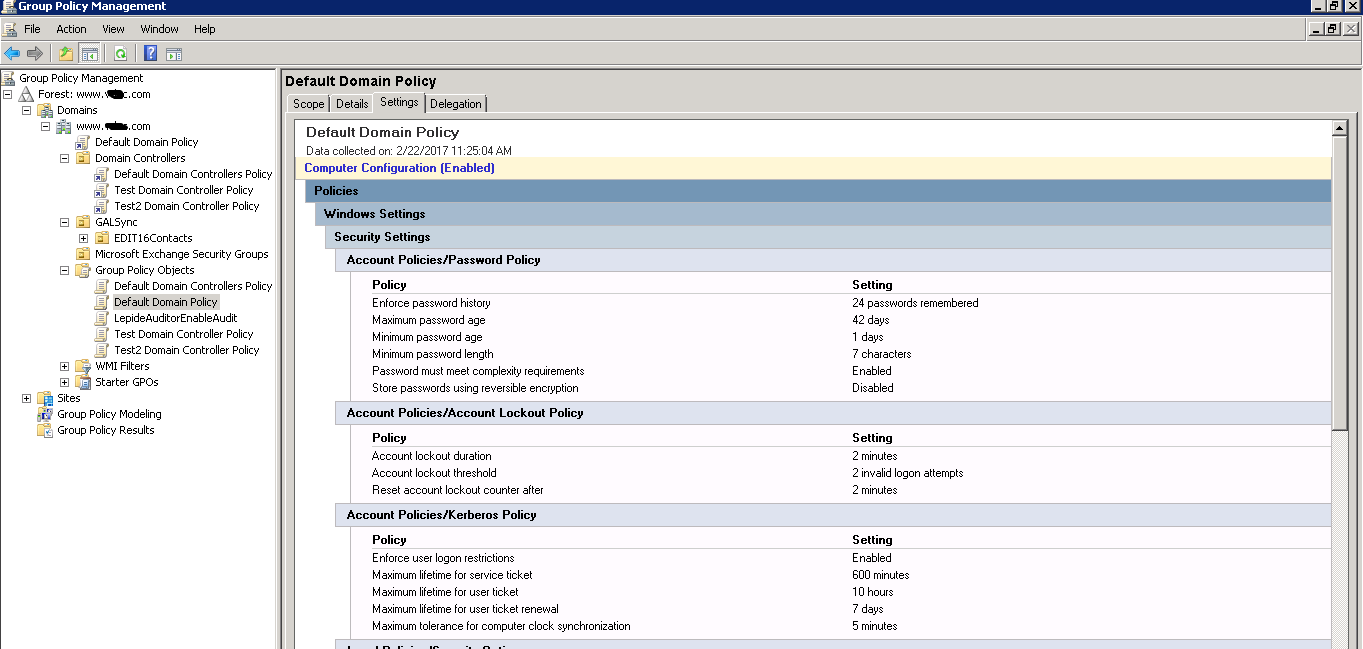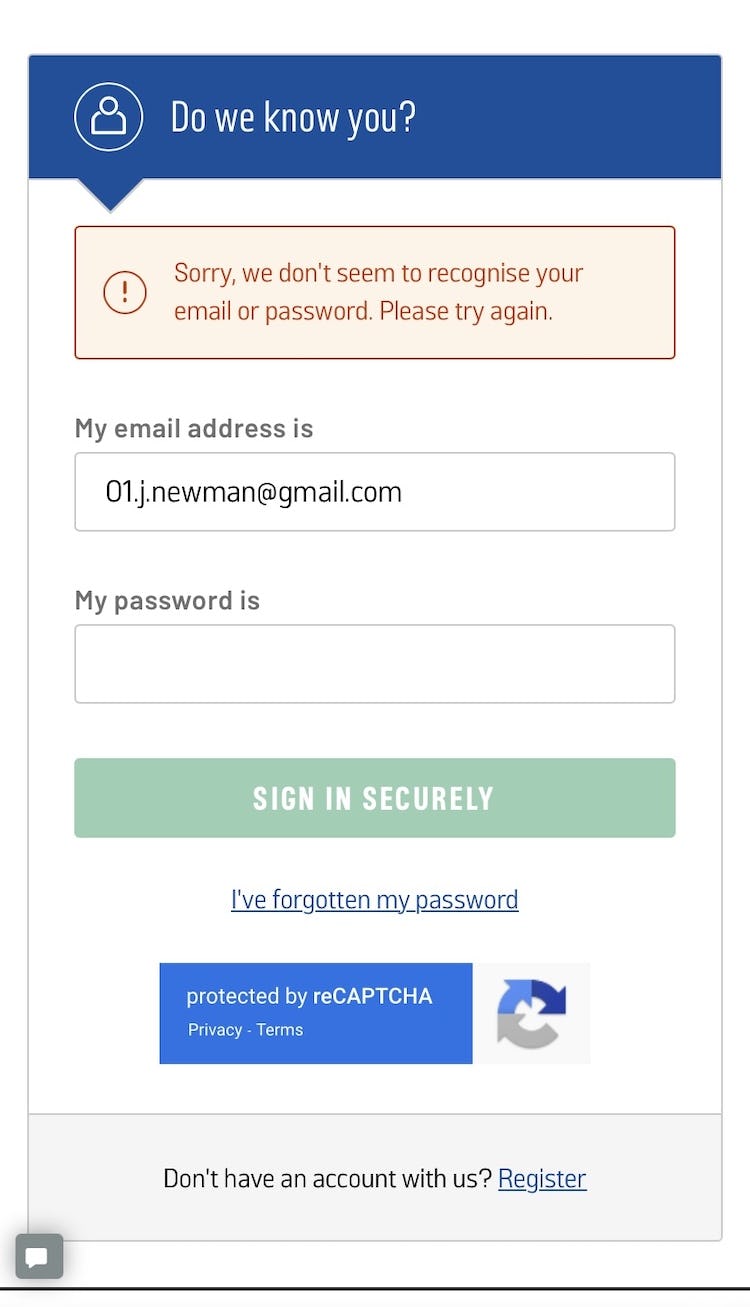
Avoid Unnecessarily Complex Password-Creation Requirements (82% Don't) – Articles – Baymard Institute
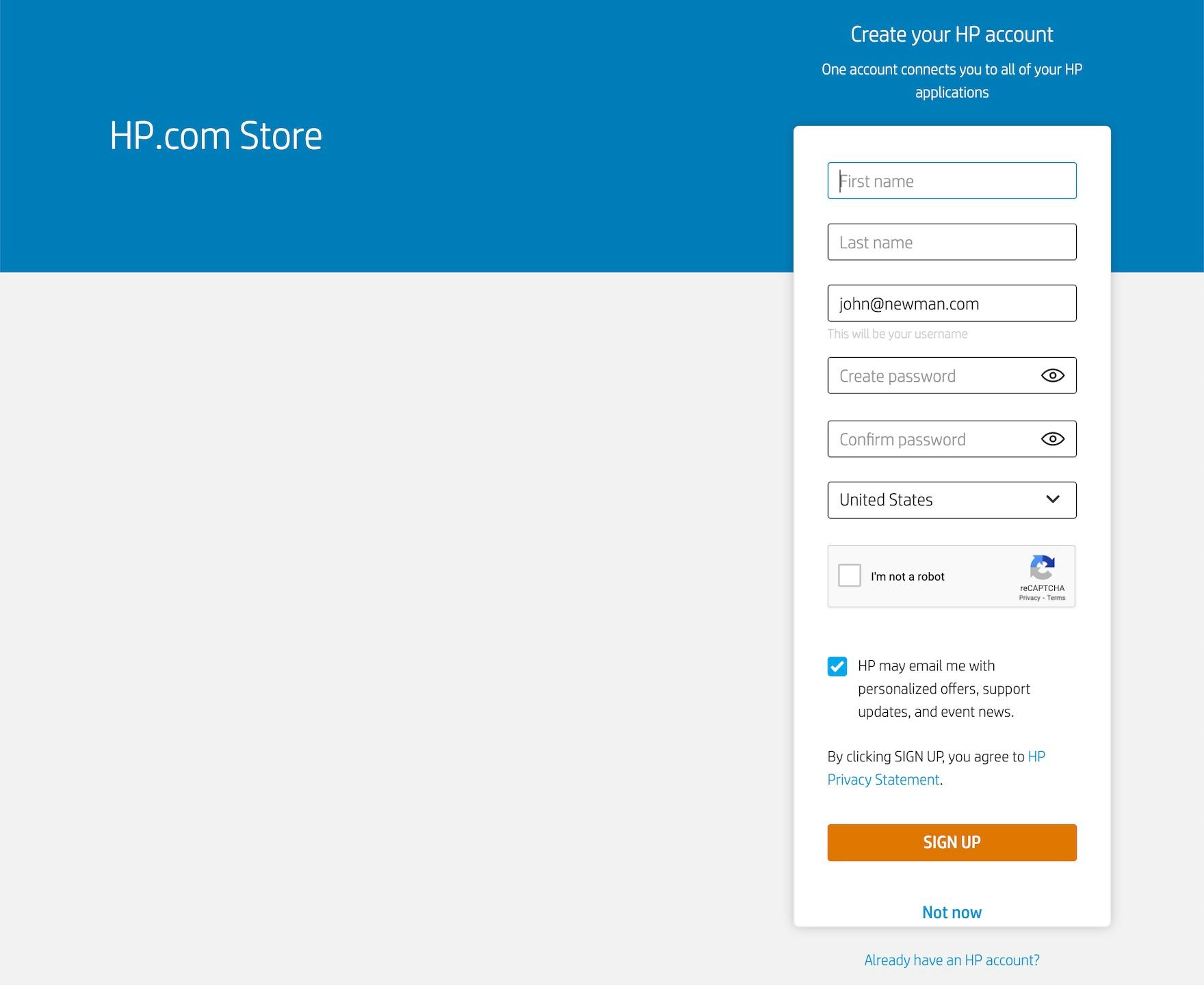
Avoid Unnecessarily Complex Password-Creation Requirements (82% Don't) – Articles – Baymard Institute

Amazon.com: StarTech.com Biometric Enclosure - Encrypted USB 3.0 2.5" SATA Hard Drive Enclosure - Fingerprint/Password Access - 256-bit AES Data Encryption - Secure External USB 3.1 Gen 1 to HDD/SSD (S251BMU3FP) : Electronics

Avoid Unnecessarily Complex Password-Creation Requirements (82% Don't) – Articles – Baymard Institute

AIS Password: What is the password to open Annual Information Statement (AIS) after downloading - The Economic Times
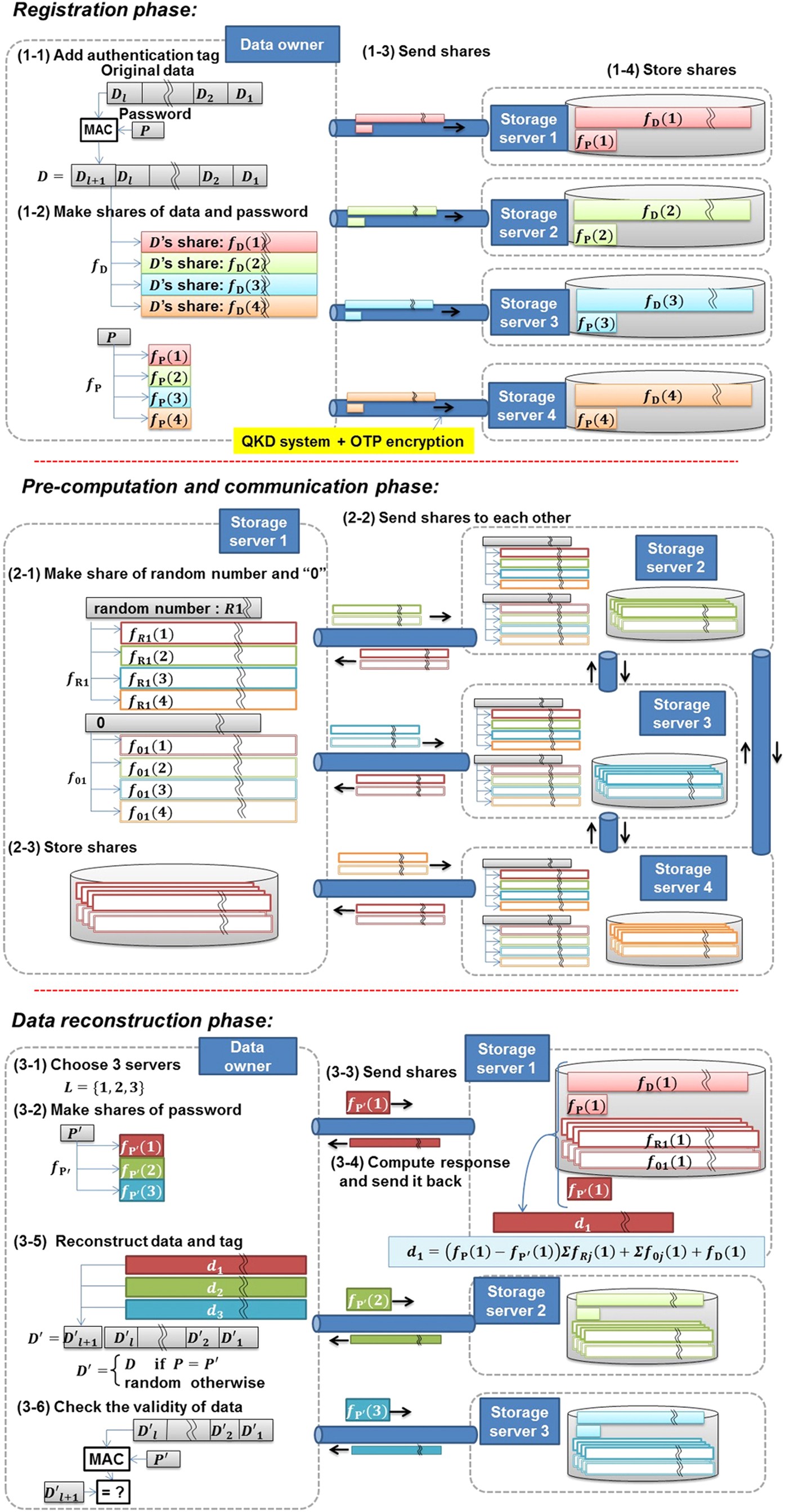
![PDF] DATA HIDING IN IMAGE BASED AUTHENTICATION USING COMBINATION OF ZERO-KNOWLEDGE PROTOCOL AND STEGANOGRAPHY NURUL NADZIRAH BT ADNAN | Semantic Scholar PDF] DATA HIDING IN IMAGE BASED AUTHENTICATION USING COMBINATION OF ZERO-KNOWLEDGE PROTOCOL AND STEGANOGRAPHY NURUL NADZIRAH BT ADNAN | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/208e0b8c6778e7f2d418dcca74fd29c1705bb6a1/40-Figure1-1.png)
PDF] DATA HIDING IN IMAGE BASED AUTHENTICATION USING COMBINATION OF ZERO-KNOWLEDGE PROTOCOL AND STEGANOGRAPHY NURUL NADZIRAH BT ADNAN | Semantic Scholar

The Man Tries To Pick Up Blocks with the Word Data. Digital Data Integrity and Security Vulnerability Concept Stock Photo - Image of data, internet: 211493740



![title %] title %]](https://ultrascan3.aucsolutions.com/manual3/images/config.png)