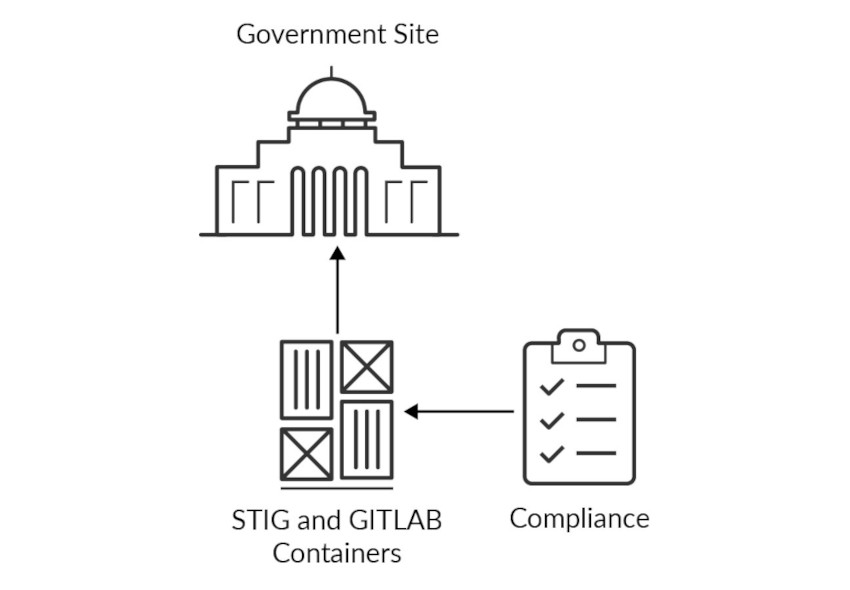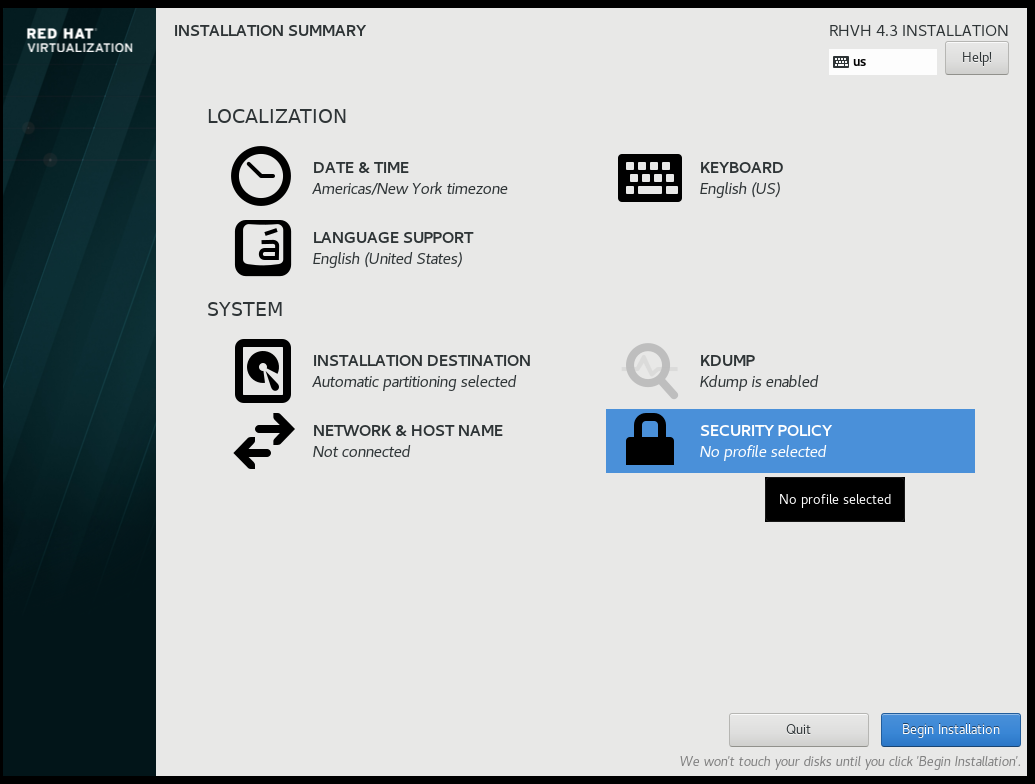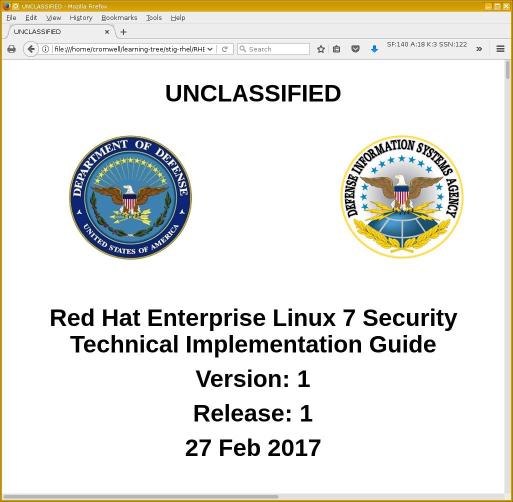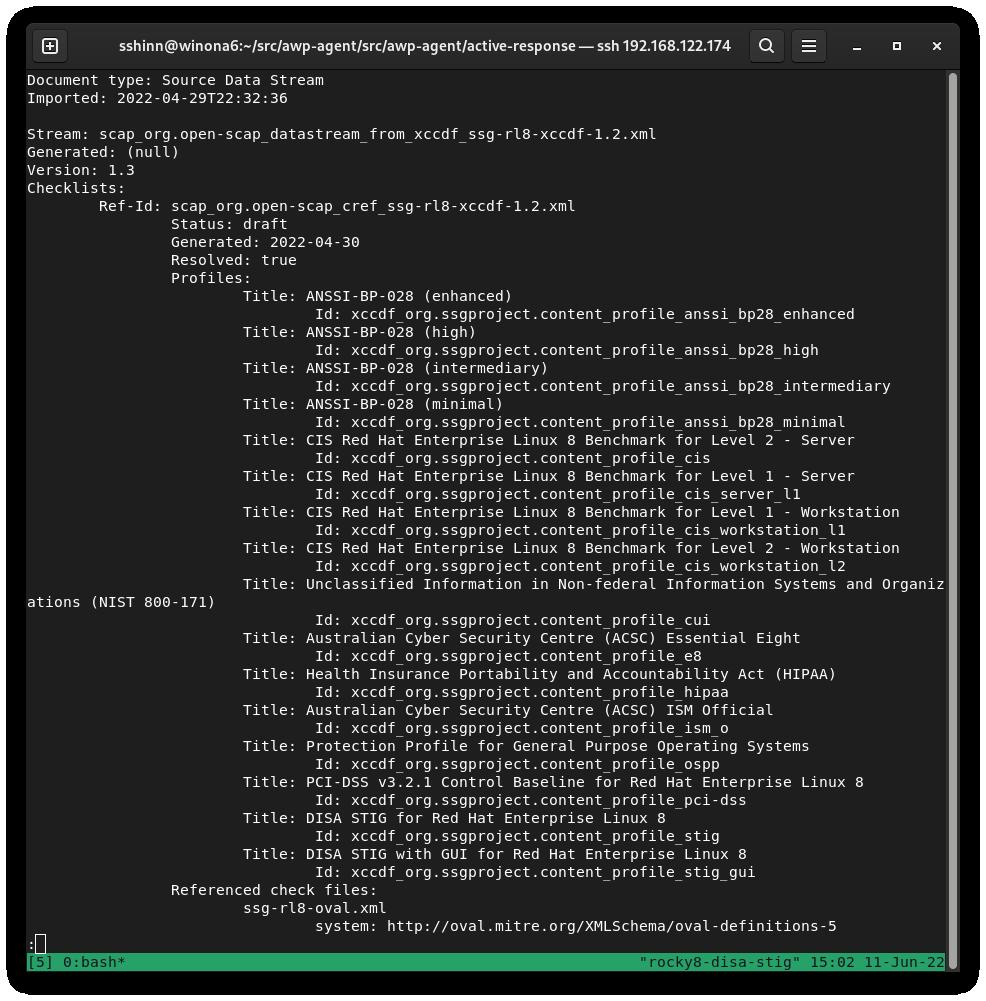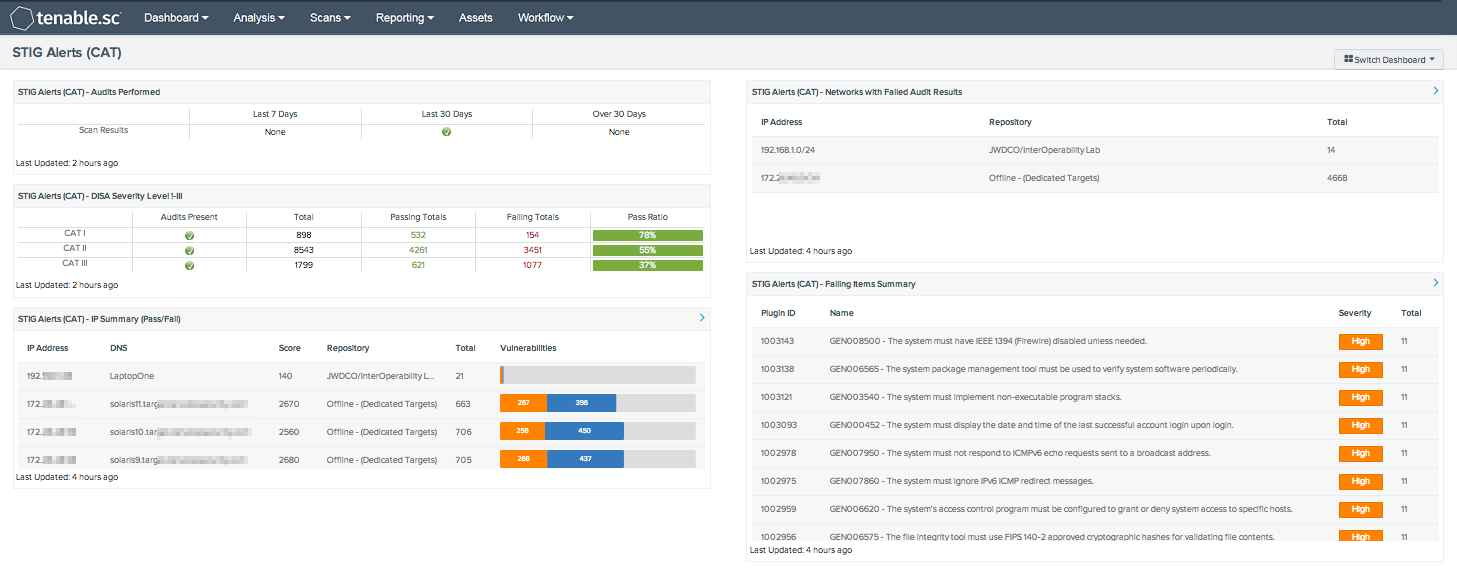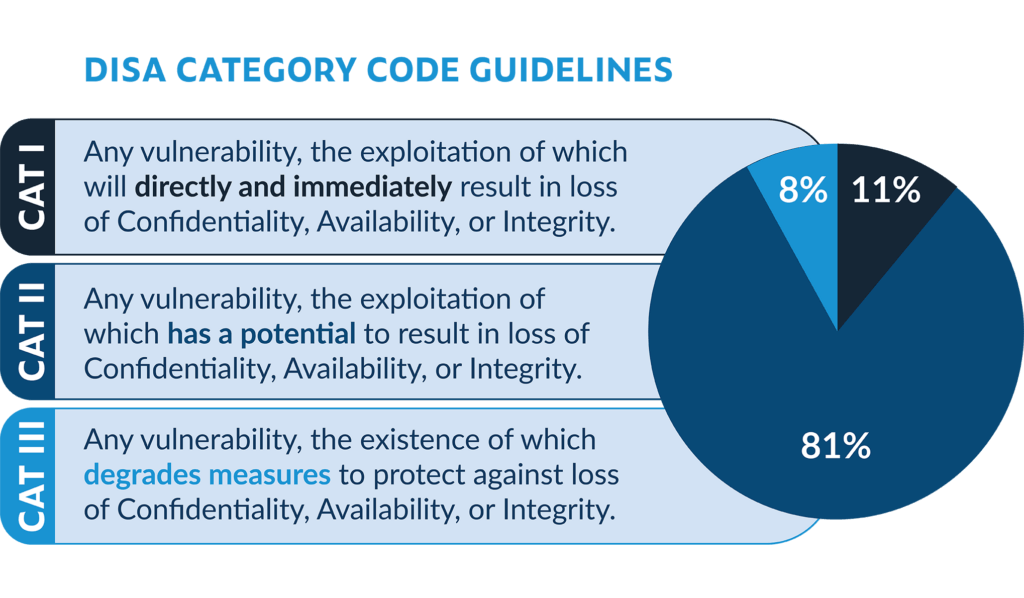
What Is STIG (Security Technical Implementation Guides)? (from DISA (Defense Information Systems Agency))

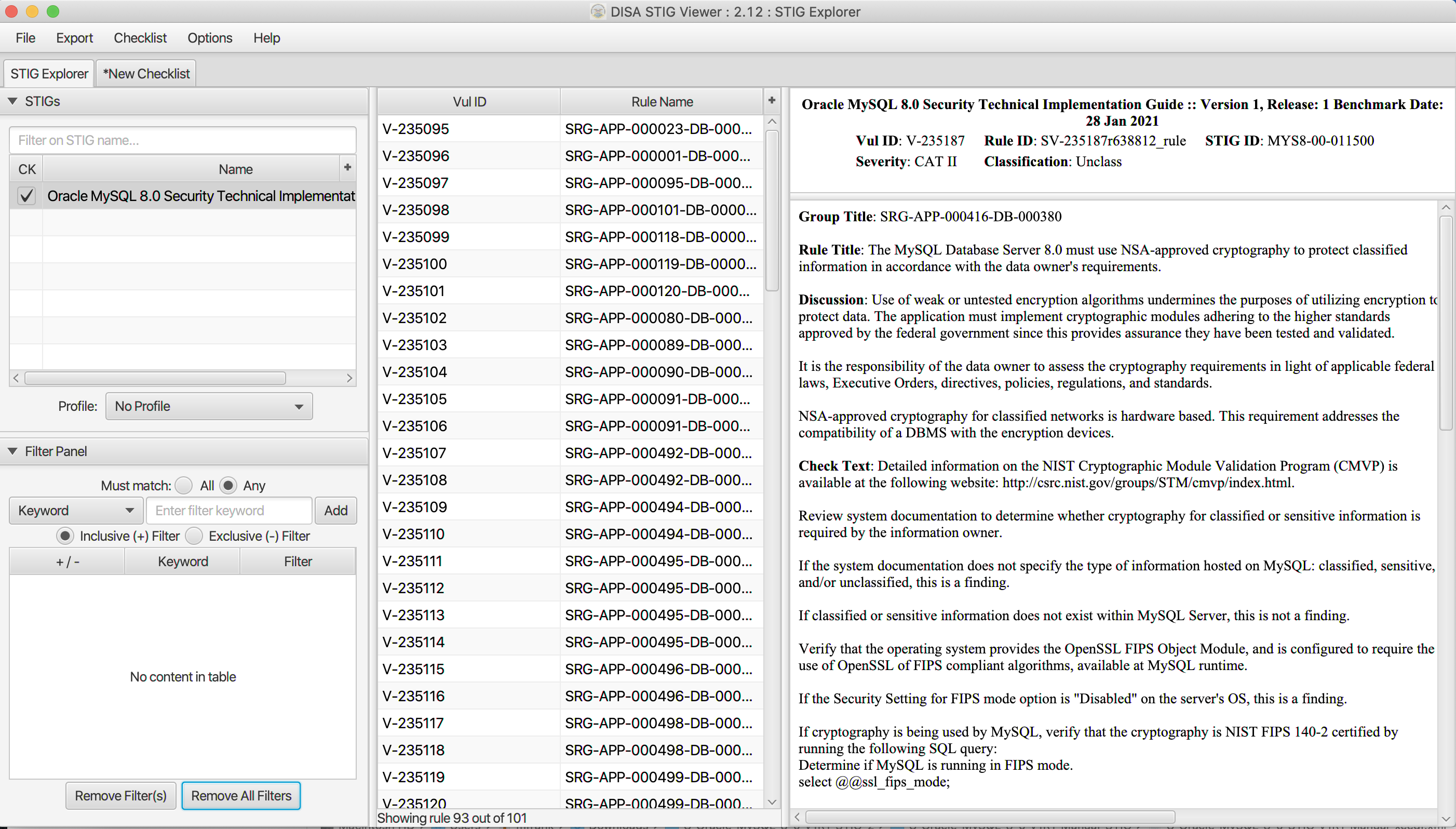
How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems

How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems