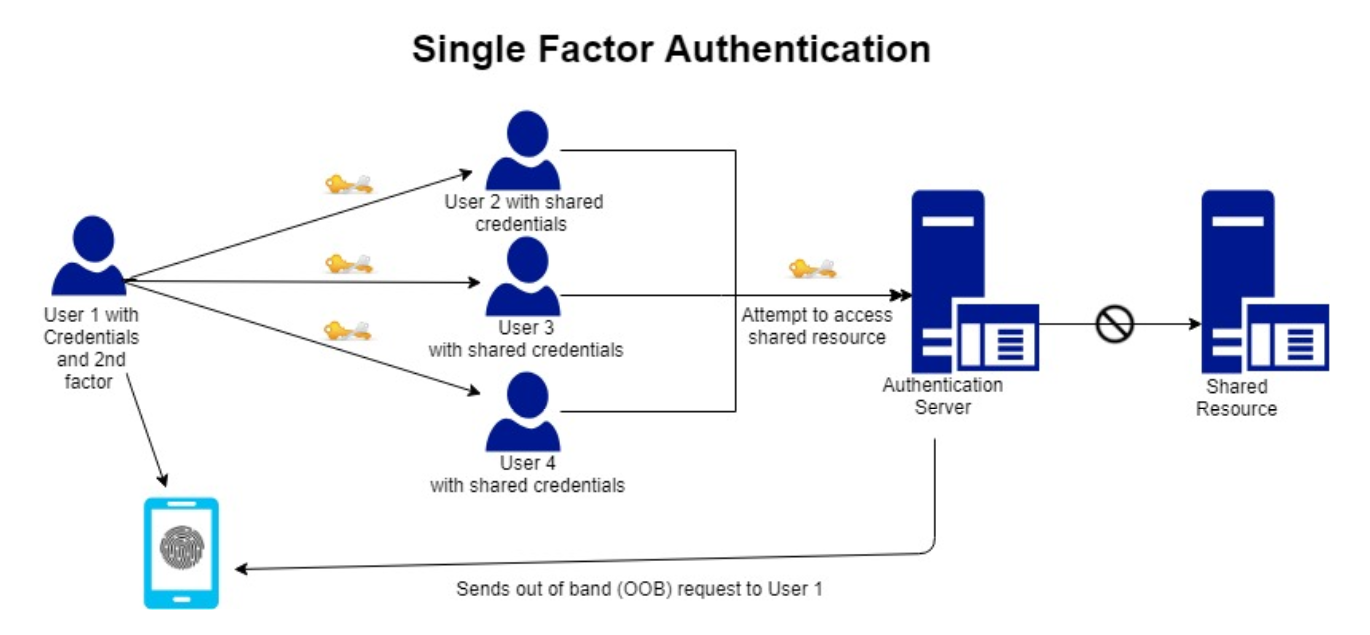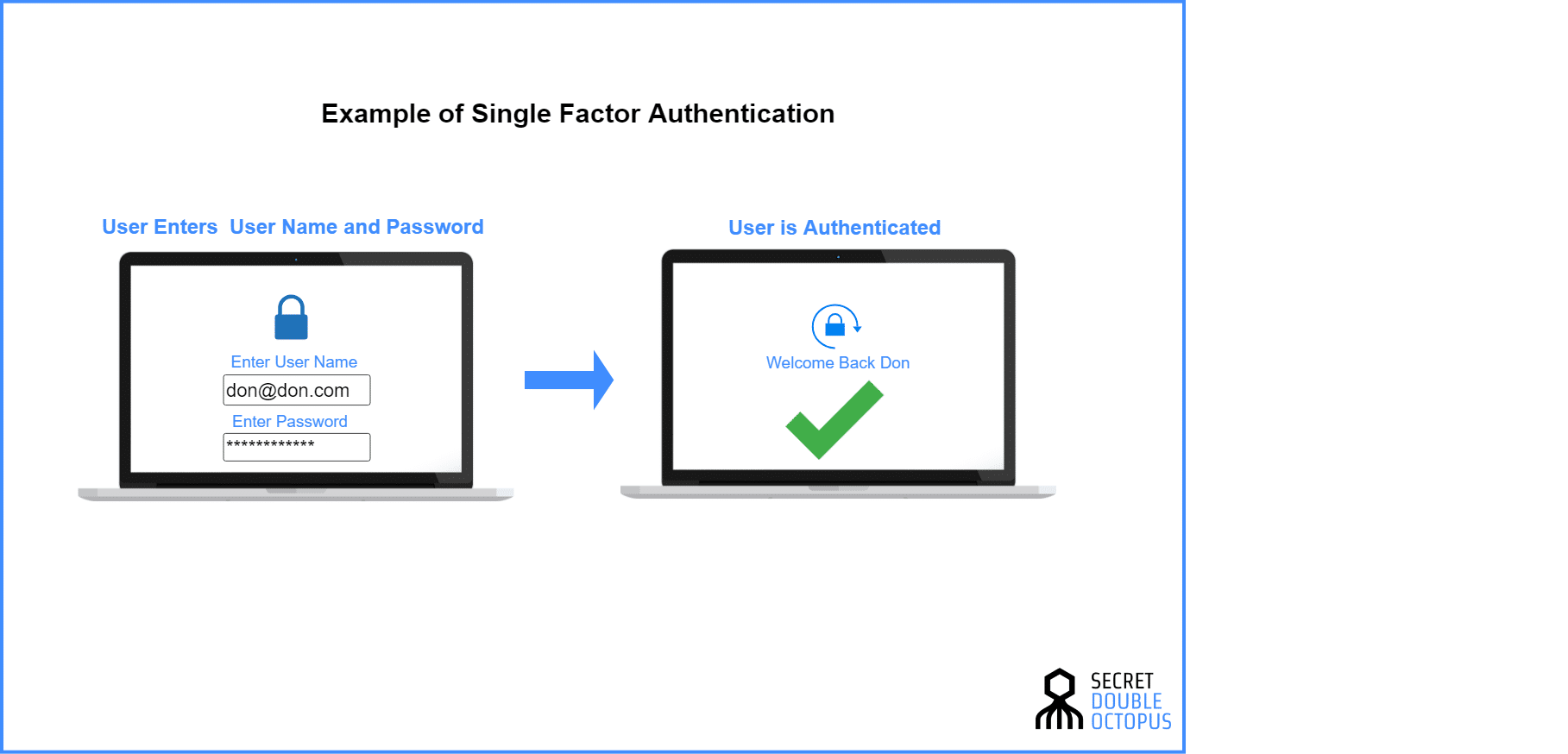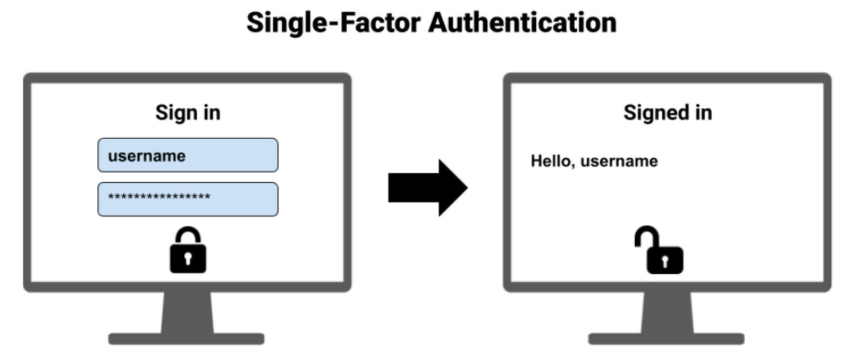
Kenali Two-Factor Authentication dan Pola Adopsinya - Jurusan Informatika - Fakultas Teknologi Industri - Universitas Islam Indonesia
Single Factor Authentication Ppt Powerpoint Presentation Gallery Good Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Single Factor Authentication Pros Cons Ppt Powerpoint Presentation Outline Graphic Tips Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates


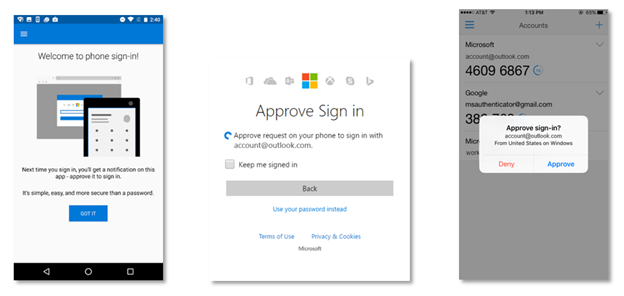

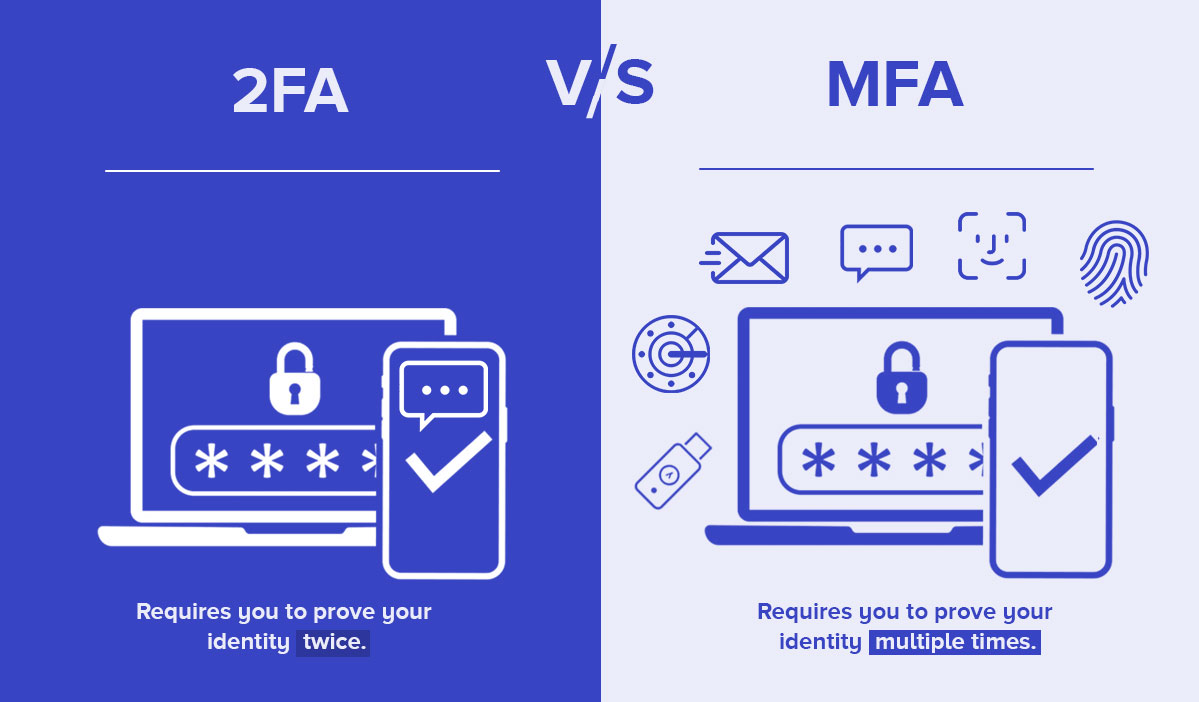
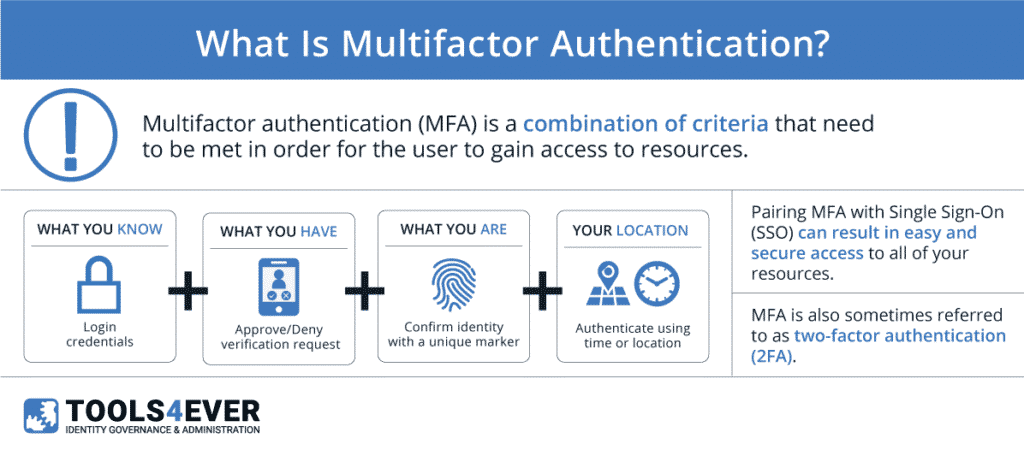



![PDF] Multi-Factor Authentication: A Survey | Semantic Scholar PDF] Multi-Factor Authentication: A Survey | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bde2549bd077adccd505b9c2bf0b92f8051b3b3f/4-Figure2-1.png)