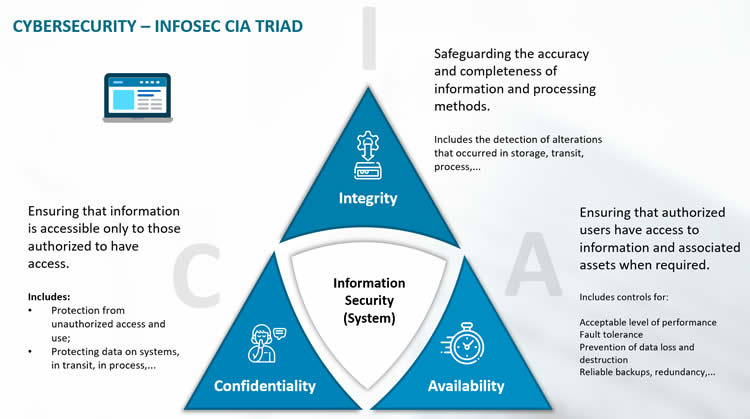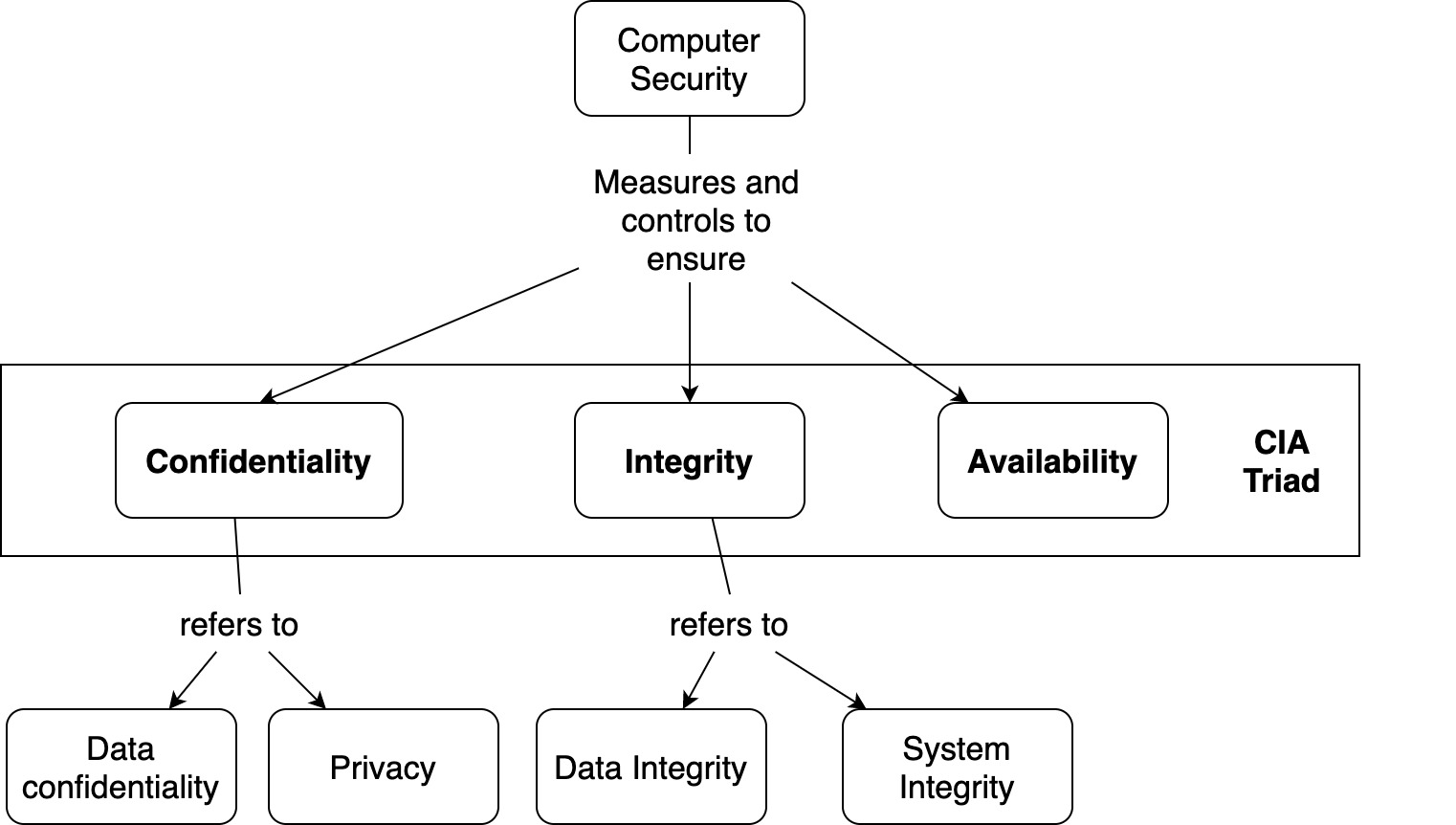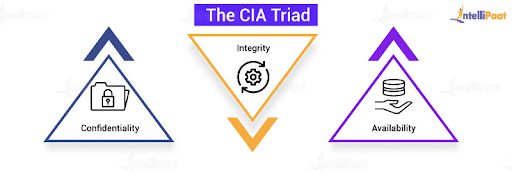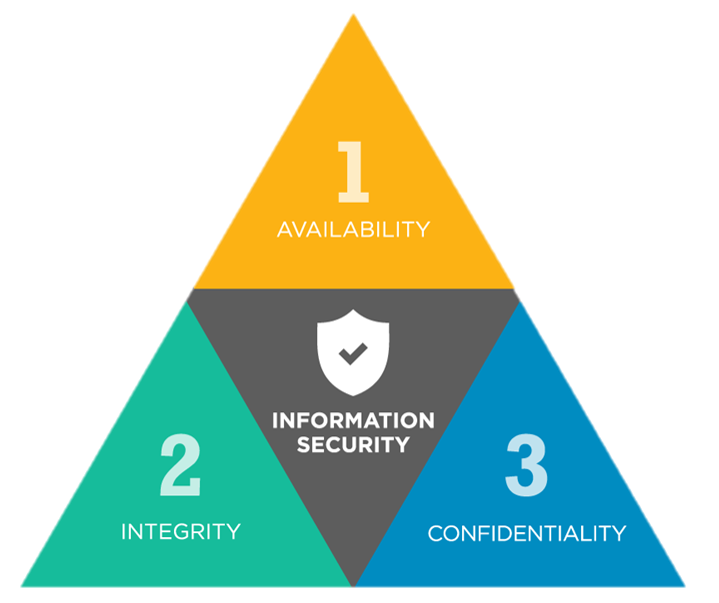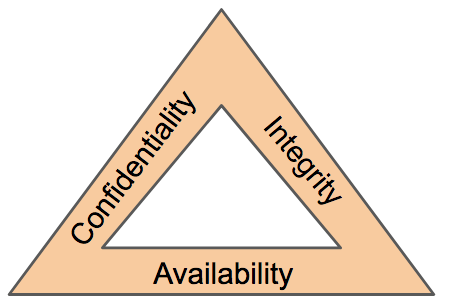
Cia Triad Of Information Security In Data Availability | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Confidentiality Integrity Availability Stock Illustrations – 34 Confidentiality Integrity Availability Stock Illustrations, Vectors & Clipart - Dreamstime